Menu
- 130 King Street West, Suite 1800
- P.O. Box 427
- Toronto, ON, Canada M5X 1E3
- (416) 865-3392
- info@triparagon.com
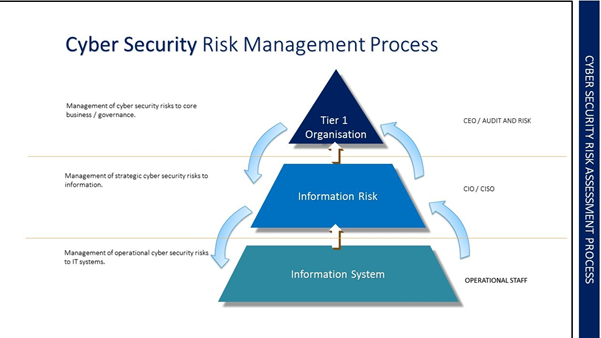
Translating a cyber security strategy and vision into action requires the buy-in and support of the wider organisation. This can be achieved by establishing a committee containing key stakeholders from across the business. The main objective of the steering committee is to achieve consensus and align cyber security priorities with the organisation’s objectives. Steering committees are most effective when they contain representatives who can make decisions on resource allocation, prioritisation, and direct cyber security activities.

Cyber threats are now the most effective way to attack an organisation and the fact is that those with malicious intent are finding ever more sophisticated ways of carrying out their activities. According to the Bank of England’s Financial Stability Report, 25% of banks perceive cyber attack as a major risk.
While phishing attacks, cloning Wi-Fi networks and obtaining passwords are all widely, and successfully, used to compromise corporate information and processes, cyber security can also be undermined by physical means – or the human threat. Cyber security technology may critical but is only effective when processes are in place to keep it that way.
Silos’ approach leaves companies vulnerable
Yet some companies persist with a fragmented approach to security and risk management that is the result of an outdated, silo-based corporate structure. It leaves an organisation vulnerable to loss of data and disruptions to continuity of service, something that could be prevented by adopting a convergence-based approach to security.
The converged approach to security
A converged approach to security highlights vulnerabilities in three areas – physical, people and process risks – across infrastructure, operations, and specific events. Convergence is being driven by the way technology is configured – as physical security systems are increasingly networked and more IT dependent, IT and network security is now crucial to the integrity of these systems.
While there is no shortage of horror stories about what can happen because of a cyber attack, for most businesses, anecdotal evidence is usually ineffective and a belief that “it won’t happen to me” pervades. For these companies it often takes a security scare before they seriously start to address the risks that they face – unfortunately, by then the damage could already have been done.
The biggest barrier to adopting a collaborative and inclusive approach to dealing with risk has little to do with external influences and everything to do with internal cross-departmental cultures.
In other words, the physical security and IT teams are not communicating effectively to better understand their respective roles and how they are, in fact, reliant on each other to keep business operations safe from harm.
The requirement for physical and IT security to collaborate in combating sophisticated threats challenges both functions to dovetail their capabilities effectively, although many struggle with identifying interdependencies and vulnerabilities.

Mapping assets and processes
However, once they have addressed this issue, organisations can develop a system that combines technology, processes, safeguards, management, and systems into a single integrated security risk framework.
A comprehensive evaluation of cyber risk requires a meticulous approach to mapping an organisation’s assets and processes through the completion of completely unbiased vulnerability and impact assessments. Only once completed and analysed can the correct response be configured.
Stakeholders buy-in
While all the above is vital, so too is stakeholder buy-in. Processes and training are needed to ensure that all employees are security aware, and this should be considered as a priority to building effective prevention, detection, and response.
Security processes are entirely dependent upon implementation of policy – therefore strict adherence is required to mitigate the possibility of a security breach. It is important to note that this should extend all the way up the corporate hierarchy, as management of the converged approach needs to be led at the highest level to ensure effective integration, oversight, and budget allocation.
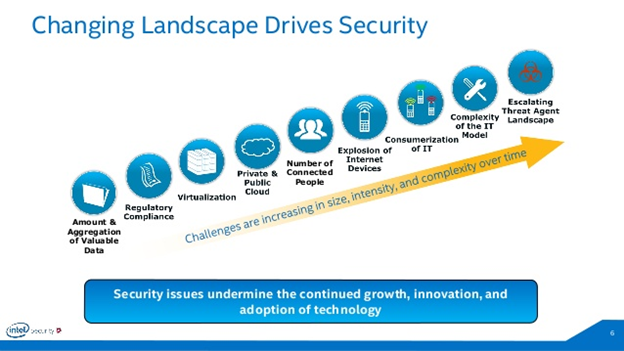
Evolving threats
The level and type of threats are constantly evolving, and organisations should review and test their systems regularly. The process of simulating real-world attacks and assessing the performance of security apparatus to determine its strengths and weaknesses is key if organisations are to be prepared. This is not only because “practice makes perfect” but because it develops a preoccupation with “what if” scenarios, and how to deal with them effectively.
A converged approach to risk and security is by far the most effective way to deal with the increasing threat posed by cyber crime. Fortunately, a growing number of organisations are starting to recognise why – is yours one of them?
Tri-Paragon’s Senior Consultants are here to assist in organizing, planning, and managing your program to achieve the desired results within your budget and resource limitations.