Bill Back Business Units and Customers for the Energy Used
Today, it’s becoming more common for organizations to have green data center initiatives to drive energy-efficient behaviors both from internal and external customers.
Today, it’s becoming more common for organizations to have green data center initiatives to drive energy-efficient behaviors both from internal and external customers.

Tri-Paragon’s Acronis Cyber Protect Cloud has features that map to the National Institute of Standards and Technology’s (NIST) security framework, combines the most needed security, policy management, and data protection technologies in one platform.
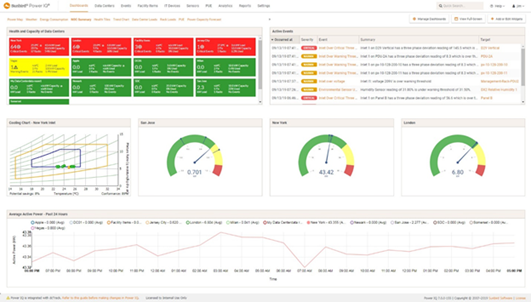
If your data center infrastructure is outdated or your data center’s utilization of space, power, and cooling resources is inefficient, you stand to benefit greatly from consolidation and virtualization efforts that will decrease the number of physical assets you have and the associated resources they consume.
Did you know?
Phishing is a type of online scam where an attacker impersonates legitimate organizations via email, text message or advertisement to trick a victim into revealing sensitive information to the attacker, or to deploy malicious software on the victim’s infrastructure.
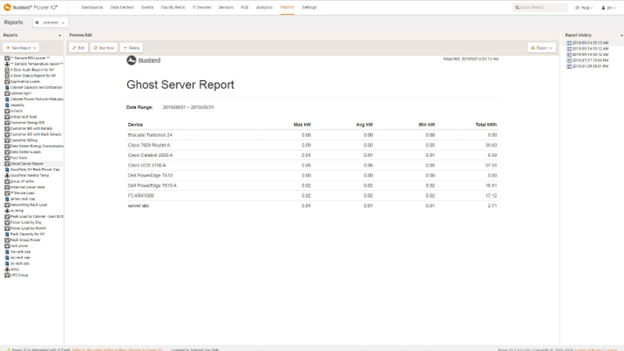
Up to 30% of servers may be “ghost servers” or “zombies”—idle servers that are physically running and consuming energy but are not performing any useful functions.

Data protection is the process of safeguarding important information from corruption, compromise, or loss. The importance of data protection increases as the amount of data created and stored continues to grow at unprecedented rates. There is also little tolerance for downtime that can make it impossible to access important information.
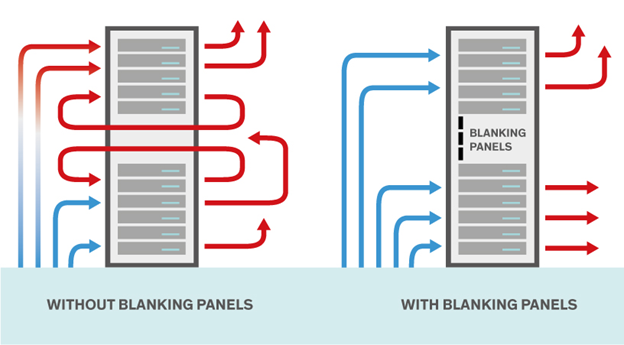
Cooling accounts for about half a data center’s energy consumption, so improving the efficiency of your cooling infrastructure is critical for improving overall efficiency. One often-overlooked way to achieve this is by optimizing airflow.

Backup and recovery is the process of duplicating data and storing it in a secure place in case of loss or damage, and then restoring that data to a location — the original one or a safe alternative — so it can be again used in operations. Ideally, this backup copy (often called a snapshot) is immutable meaning it cannot be altered after it is created to protect against mutations such as ransomware.