Menu
- 130 King Street West, Suite 1800
- P.O. Box 427
- Toronto, ON, Canada M5X 1E3
- (416) 865-3392
- info@triparagon.com
Here is what you need to know about the NIST’s Cybersecurity Framework. The tech world has a problem: security fragmentation. There is no standard set of rules–or even language–used to address the growing threats of hackers, ransomware, and stolen data, and the threat only continues to grow.
Broadly speaking, the NIST Framework is widely viewed as being a good starting point for building strong cybersecurity programs. However, when designing or updating existing cybersecurity programs, organizations should ensure that they customize it based on their needs and industry requirements (including regulatory requirements). Canadian organizations should take this opportunity to revise their existing cybersecurity programs to ensure that they meet the minimal requirements of the new NIST Framework.
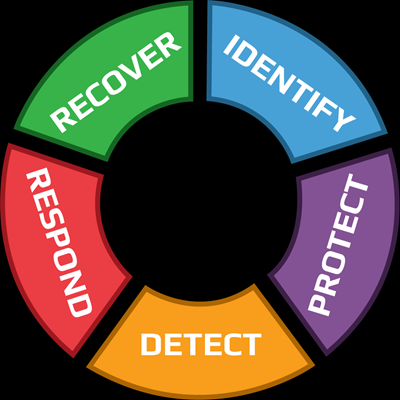
The Cyber Security Framework is divided into three primary components:
Desired cybersecurity outcomes organized in a hierarchy and aligned to more detailed guidance and controls. This part provides a comprehensive list of all industry standards, guidelines, and practices applicable to each cybersecurity topic listed in the Framework. It enables the executive branch of an organization to properly communicate their cybersecurity objectives and reach their desired operational outcomes
Alignment of an organization’s requirements and objectives, risk appetite and resources using the desired outcomes of the Framework Core. This part is intended to help establish a roadmap for reducing cybersecurity risks that is well-aligned with organizational and sector goals, considers legal/regulatory requirements and industry best practices and reflects risk management priorities. It can be used to describe both the current state and the desired state of specific cybersecurity activities.
A qualitative measure of organizational cybersecurity risk management practices. This part aims to assist organizations in assessing the cybersecurity risks they face and the processes they have in place to manage such risks. The degree of rigor and sophistication in the cybersecurity risk management practices of the business are measured on a scale ranging from “Partial (Tier 1)” to “Adaptive (Tier 4).” Organizations can select the most appropriate Tier depending on their current risk management practices, threat environment or legal and regulatory requirements specific to their industry.
Three Critical Questions to ask yourself
Tri-Paragon recommends taking a proactive approach to prevention and mitigating identified loopholes before a breach takes place to minimize your risk.
How?
Performing an assessment of your Cyber Security practices by completing our automated security assessment questionnaire.
Our cyber security assessment checklist is based on using the NIST Cyber Security Framework standard’s core functions of Identify, Protect, Detect, Respond, and Recover.
Collectively, this framework can help to reduce your organization’s cybersecurity risk. Our checklist is a great resource to assist you in your evaluation of your facility’s cybersecurity. Once you have answered all the questions, we will provide you with our assessment report along with our recommendations of what you should do to mitigate your exposures. You can choose to action the report internally, request our coaching assistance, have us implement the recommendations or choose to ignore it at your own peril.
Cost of a Cyber Security Assessment: $5,000.
What is the cost of a breach?
To get started: