Menu
- 130 King Street West, Suite 1800
- P.O. Box 427
- Toronto, ON, Canada M5X 1E3
- (416) 865-3392
- info@triparagon.com
Tri-Paragon Inc. 130 King Street West, Suite 1800, P.O. Box 427, Toronto, ON Canada M5X 1E3
Phone: 416.865.3392 Email: info@triparagon.com
(The science of performance)
“If you think it is expensive to hire a professional to do the job, wait until you hire an amateur” Red Adair
Disaster Recovery Plan Consists of 2 primary inputs- Business Impact Assessment and Risk Analysis
Business Impact Analysis and Risk Assessment are both important components of BC/DR Plans. However, Business Impact Analysis should be carried out before attempting Risk Assessment. Once both these components are in place, it is easier to formulate a sound strategy and plan for Business Continuity / Disaster Recovery.
The four most important risk scenarios that affect business operations of an organization are:

The responses to the above risk scenarios give an insight into the dangers the organization faces during a disaster. There are other risks too, but the above are the major risks. Once the risks have been identified, its impact on different aspects of production, distribution and services can be measured. Those risks which affect mission-critical operations should be handled first.
The recommended strategy used to handle risks:
Using the Business Impact Analysis to gauge the impact of a specific risk on business operations from the standpoint of restarting production as well as its financial impact determines its mitigation strategy and importance.
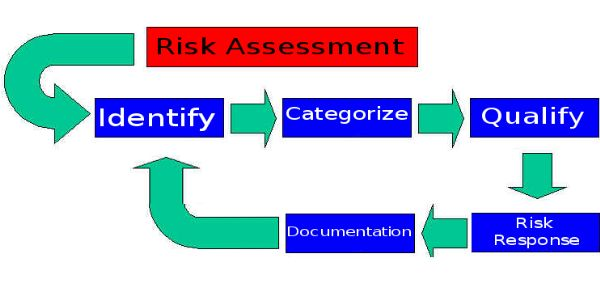
To get started with a risk assessment, begin by identifying the most critical business processes from the BIA. You should then gather information on potential threats to your organization.
There are numerous sources available to help you gather threat information, such as:
These sources can help you determine the likelihood of specific events occurring, as well as the severity of actual events. You can rule out certain events if there is almost no chance of them occurring. A risk analysis involves identifying a risk, assessing the likelihood of an event occurring and defining the severity of the event’s consequences. It may also be useful to conduct a vulnerability assessment, which can help identify situations in which the organization may be putting itself at increased risk by not performing certain activities. An example may be the increased risk of viruses by not using the most current antivirus software.
Finally, the risk analysis results should be summarized in a report to management, with recommended mitigation activities.
Types of defensive responses
After the risks and vulnerabilities have been identified, defensive responses can be considered.
The sequence in which these measures are implemented depends to a large extent upon the results of the risk assessment. After you identify a specific threat and its associated vulnerability, you can plan the most effective defensive strategy. Remember that contingency plans must cope with the effects, regardless of the causes.
Types of hazards
Hazards are unique combinations of events and circumstances. The two primary categories are man-made and natural.
Man-made hazards are those in which an individual or multiple persons may be held accountable for contributing to the event(s) that caused a disaster. This could be through deliberate or accidental causes. Natural hazards are typically considered Acts of God for which there is no one to blame, such as with the weather, earthquakes, floods and fires. If your organization is in an area prone to hurricanes, or if your building has construction vulnerabilities, that should be noted in your risk assessment.
Grouping impacts
After the risks have been identified, you’ll want to identify the potential effects, symptoms and consequences resulting from the event.
Basic effects: There are five basic effects that can have disastrous consequences:
Symptoms: The perceived symptoms might be a loss (or lack of):
Consequences: Secondary effects or consequences might include:
Types of risk assessments
Risk assessments generally take one of two forms: quantitative, which seeks to identify the risks and quantify them based on a numeric scale (e.g., 0.0 to 1.0 or 1 to 10); and qualitative, which is based on gaining a general impression about the risks so as to qualify them. The process uses subjective terms like low to medium, high to poor, and good to excellent, instead of numeric values.
Quantitative methods, which assign a numeric value to the risk, usually require access to reliable statistics to project the future likelihood of risk. As mentioned earlier, qualitative methods often include subjective measures, like low, medium and high. However, sometimes the qualitative approach is more acceptable to management.

A basic formula, Risk = Likelihood x Impact, is typically used to compute a risk value. This formula is also known as a risk assessment matrix. By weighing the likelihood of an event against the level of damage it could cause, the risk assessment matrix is an illustrative tool for management to use to plan for possible disasters.
For example, we can use a scale of 0.0 to 1.0, in which 0.0 means the threat is not likely to occur and 1.0 means the threat will absolutely occur. The impact 0.0 means there is no damage or disruption to the organization, whereas 1.0 could mean the company is completely destroyed and unable to further conduct business. Numbers in between can represent the result of a statistical analysis of threat data and company experience. Using the quantitative range 0.0 to 1.0, you may decide to assign qualitative terms to results (e.g., 0.0 to 0.4 = low risk, 0.5 to 0.7 = moderate risk, and 0.8 to 1.0 = high risk).
Once all the relevant risks have been analyzed and assigned a qualitative category, you can then examine strategies to deal with only the highest risks or you can address all the risk categories. The risk management plan will depend on management’s risk appetite, which is their willingness to deal appropriately with risks. The strategies you define for risks can next be used to help design business continuity and disaster recovery strategies.
Conducting your risk assessment: Who, what, when
An appointed project manager and their team are typically in charge of conducing a risk assessment and risk management plan. Personnel may be involved when it comes to actions that may need to be performed at that level in the future.
Depending on the number of effects, symptoms and consequences, the level of detail in a risk assessment will vary by organization. There is no set number of risks to look for in a general risk assessment, so that is up to the discretion of the company performing the assessment.
A risk assessment is a key activity in a business continuity or disaster recovery program. The process can be relatively simple; for example, if you elect to use a qualitative approach. They can be more rigorous when using a quantitative approach, as you may want to be able to substantiate your numerical factors with statistical evidence.
How often you carry out a risk assessment is also up to your discretion. However, results should be updated periodically to determine if any changes to the risks (e.g., likelihood and impact) have occurred. Regardless of the methodology used, the results should map to the critical business processes identified in the business impact analysis and help define strategies for responding to the identified risks. If a risk assessment is out of date, so are the strategies used to combat potential hazards.
Using the Business Impact Analysis and the Risk Assessment documents as input, an effective Disaster Recovery and Business Interruption Plan can be created to protect the business from most unexpected business interruptions be they technological or otherwise.